Home / Platform Considerations
Microsoft Exchange 2010 – 2019 (EWS) Considerations
Transend supports migrating to or from Exchange versions 2010 – 2019 via Exchange Web Services (EWS).
Authentication
When performing a migration of bulk users using admin credentials (a service account so that you don’t need end-user passwords), you will need to use Basic Authentication:
- Basic Authentication
- Impersonation
- Delegation
Assign an Application Impersonation role to your migration account in Exchange Server via EWS, Exchange Web Services over port 443 (HTTP or HTTPS).
Assign impersonation to your migration account using the Exchange Management Console, or use Exchange PowerShell. Impersonation allows you to migrate user accounts using the migration account’s login and password so that you do not have to provide user passwords.
Setting up Impersonation in Exchange Management Console
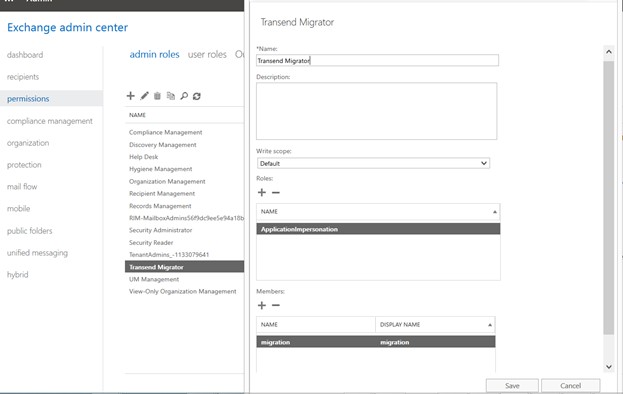
Create an Admin Role from the Exchange Admin Portal:
- Sign-in to the Exchange Admin Center using an Admin account.
- Click Permissions from the menu on the left hand side of the screen.
- Click on Admin roles from the top menu.
- Click on the Add a new Admin Role Group icon.
- Name: Transend Migration Console
- Select: ApplicationImpersonation Role
- Add the migration account: [email protected] (or name the account whatever you desire)
- Click Save.
- Add the Impersonation account email address and password into the configuration Settings in Transend Migration Console and click Verify.
Note: Depending on your authentication, the impersonation service account may be:
- UPN name
- Email address
- Domain\username
Use PowerShell to Assign Application Impersonation
Alternatively, you may assign impersonation to your migration account using Exchange PowerShell.
- Open the Exchange Management Shell.
- Run the New-ManagementRoleAssignment cmdlet to add the permission to impersonate to the specified user.
- Change “ServiceAccount” to the account you are assigning impersonation to.
The following example shows how to configure Application Impersonation to enable an administrator account to impersonate all user accounts in an organization:
Example:
New-ManagementRoleAssignment –Name:impersonationAssignmentName –
Role:ApplicationImpersonation –User:serviceAccount
Update Access Settings in Exchange
Effective April 2025, Microsoft has changed how Exchange Web Services (EWS) access is controlled within Exchange Online. This change impacts how administrators manage EWS access and could affect mailbox migrations.
Key Changes:
- EWS access now requires both organization-level and user-level settings to be enabled.
- Administrators can no longer be overridden by user-level settings.
- This update enhances security and policy consistency across Exchange environments.
To avoid migration disruptions, review your current EWS configurations:
- Check your organization-level EWS setting.
- Verify user-level settings for mailboxes that require EWS access.
- Adjust settings as necessary to ensure uninterrupted migrations.
Learn more about how to control EWS usage in Exchange Online.